Remote device threats are rising fast with hybrid work. IT teams need visibility, control, and speed. Organizations are using tools like ManageEngine Endpoint Central to deal with issues like patching, mobile management, security, and compliance. Find out how modern teams fight endpoint chaos and stay ahead.
On this page
One morning. Three emails. One laptop crashes during a Zoom call, and another user’s phone syncs with unauthorized cloud storage. A third flags a delay in getting critical patches.
Today’s IT teams sit in the hot seat of modern device sprawl. Laptops at home. Phones on the move. Tablets running legacy systems. And desktops are still sitting in office cubicles.
Each device brings its own settings, risks, and blind spots. What used to be a tightly locked perimeter now stretches across countries and time zones, resulting in serious remote device threats.
Hybrid work brought flexibility for sure. But it unfortunately increased the number of endpoints to manage. But what opened the floodgates was the BYOD policies. Employees expect frictionless access to the infrastructure, and security teams expect control. And IT departments get stuck somewhere in between, putting out fires.
This is the new normal, which has rushed past bandwidth or budgets. Now it’s about visibility and control. And one hard truth: organizations can’t secure what they can’t manage. The sprawl is real, and Remote Device Threats have officially become the IT department’s biggest headache.
Centralized Offices to Everywhere Networks
Rewind five years, and enterprise IT was built like a fortress. On-prem servers, tightly managed desktops, and clear access policies. Remote devices sat behind a perimeter. Firewalls did the heavy lifting, and security came easy.
Then came the shift. Hybrid work became standard, and workspaces turned fluid. And with that, the network perimeter? Gone.
Now, one team member logs in from an airport lounge. Another edits files from a cafe. Meanwhile, someone else accesses sensitive data from a personal tablet on home Wi-Fi. And it’s all happening across multiple time zones, on different operating systems, often outside company VPNs.
Add in SaaS tools, personal cloud drives, and rogue apps, and suddenly, IT teams are flying blind. Endpoint chaos is everywhere, and as a result, Remote Device Threats are on the rise.
What Keeps IT Teams Up at Night?
Every endpoint is a potential liability. Multiply that by hundreds or thousands of remote devices, and you’ll see why IT leaders stay glued to dashboards around the clock.
Patching remains one of the biggest nightmares. Remote devices slip through the cracks. Time zones delay updates. And one unpatched machine? That’s all it takes for a breach, making Remote Device Threats a serious concern for all.
Shadow IT makes it worse. Employees install unsanctioned apps just to get work done faster. The result? Unmonitored software is spreading across remote devices with zero oversight. Such software gets full access with no approval or documentation.
Then there’s compliance. Whether it’s GDPR, HIPAA, or PCI DSS, audit trails are hard to maintain when remote devices operate in silos. One missing policy update or misconfigured device can land the company in legal hot water. And with hybrid teams, that risk just multiplies.
IT teams face a constant push-pull. If they enforce too many controls, users revolt. If they loosen the reins, vulnerabilities slip in. It’s a daily balancing act.
That’s why more enterprises are shifting toward unified endpoint management. Solutions like ManageEngine Endpoint Central give IT one place to view, manage, and secure every device, no matter where it lives.
The Cost of Looking Away
When remote devices go unmanaged, things go south.
Take Workiva. A connected third-party app tied to its CRM vendor triggered a data breach. It was access misuse. But it still led to unauthorized exposure and forced a disclosure. Just one integration outside IT’s purview, and the damage was done.
Another stat? 31% of companies reported a SaaS data breach in the past year. Most weren’t massive headline-makers. But they stemmed from unsanctioned tools, unsecured endpoints, and cloud misconfigurations. Quiet risks, loud consequences.
And then there’s the productivity toll that Remote Device Threats take on the organization. Every time remote troubleshooting takes hours instead of minutes, work slows down. Teams get frustrated when deadlines stretch far beyond expectations.
And the worst part? Such incidents impact an organization’s reputation, along with its revenue. And most of it traces back to endpoints left out of the loop.
How Organizations Are Fighting Back?
The fightback is here, and it’s picking up steam. Enterprises now demand convergence. IT and security teams are working closer than ever. Device management today includes managing inventory and risk posture. Organizations are enforcing redundant policies in real-time.
The automation has a huge role to play here. Using automation, patch cycles run on schedules. Remote devices auto-enroll with pre-configured rules. Compliance checks kick in without manual intervention. The best part? This entire operation is scalable.
Zero Trust has found its way to remote devices. It’s no longer once verified, always trusted.
Every device, every session, every access, context matters. Is it the right user? Is the device secure? Is the location suspicious? If something feels off, access gets denied or flagged.
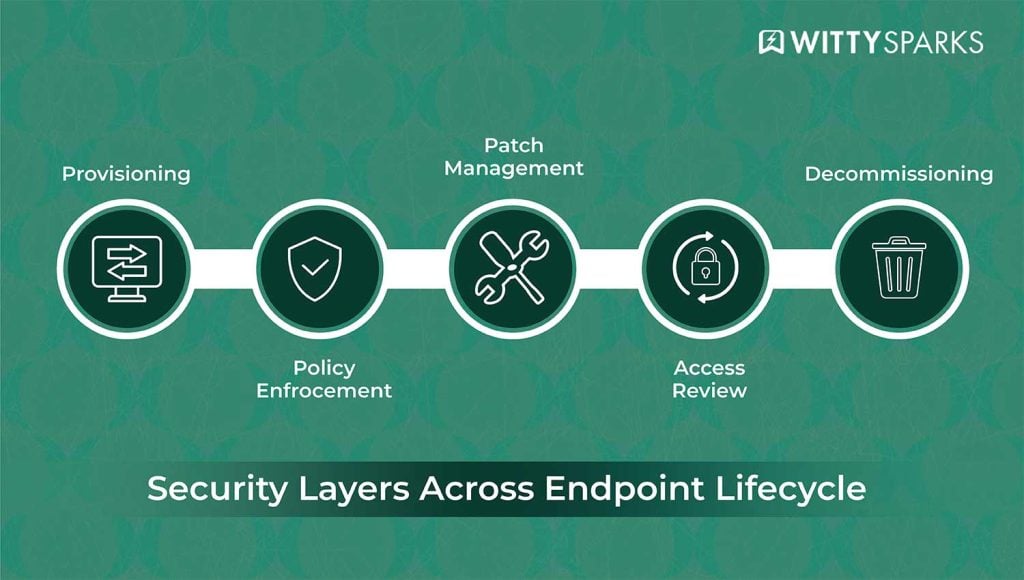
Lifecycle management is getting sharper, too. From first provisioning to final decommissioning, every touchpoint is now tracked. That includes wipe protocols, access revocation, and asset reassignment.
And leading this charge are the tools like ManageEngine Endpoint Central. These tools act like a command center for organizations. IT teams use them to push patches, control desktops remotely, enforce mobile policies, and maintain compliance across OS platforms.
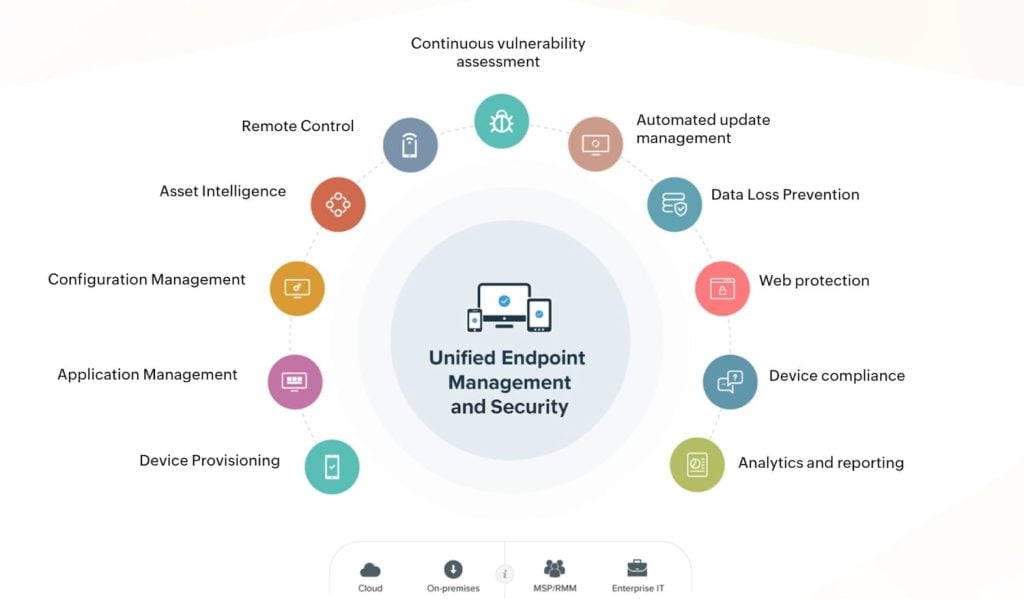
Here’s how ManageEngine Endpoint Central gives IT teams a serious edge:
- Unified Dashboard: Manage all desktops, laptops, mobiles, and servers across platforms from one console.
- Automated Patch Management: Push OS and third-party updates without manual follow-ups.
- Remote Control & Troubleshooting: Securely access and fix endpoints without waiting on users.
- Mobile Device Management (MDM): Lock, locate, wipe, and manage mobile assets on the go.
- Compliance & Audit Reporting: Generate real-time logs and policy reports to meet HIPAA, GDPR, PCI DSS, and more.
- Asset Intelligence: Track device health, usage patterns, and hardware/software inventory for smarter decisions.
- Custom Scripts & Configurations: Automate tasks across endpoints with policy-based scripts and settings.
- Role-Based Access Controls (RBAC): Fine-tune admin privileges based on roles, locations, or teams.
- Digital Employee Experience Monitoring: Keep tabs on end-user performance issues before they snowball into support tickets.
- Ransomware Protection & Attack Surface Control: Detect vulnerabilities early, block suspicious activity, and reduce exposure points across all endpoints.
The platform blends visibility and control. One dashboard and one set of rules. Organizations don’t have to hop between different tools. That unified view helps IT leaders spot vulnerabilities before they explode, and resolve them without slowing down business.
Lessons From the Field
Let’s look at the fallout and the fix.
What happens if a global law firm skips a patch for a known Windows vulnerability? It can result in major downtime, even if a single device takes a hit and the malware spreads across the entire network. This impacts the client organization itself and its people. The damage is never short of millions of dollars.
There are numerous such cases where Remote Device Threats have crumbled businesses. But the point is, a unified endpoint solution like ManageEngine Endpoint Central could’ve made the difference. Policy enforcement would have blocked risky behavior. Real-time patching would have plugged the gap.
Remote control features would’ve enabled faster responses. Audit logs would’ve ensured airtight compliance reporting. That’s what is needed to tackle Remote Device Threats.
Why Endpoint Management Is Moving Center Stage?
Endpoint management used to be backend stuff, quiet, reactive, invisible. But not anymore. Device sprawl and, as a result, Remote Device Threats, have outpaced old-school perimeter thinking. Security perimeters stretch thin when employees work across five different remote devices from five different locations.
Leaders now ask a different question: How can we control endpoints without compromising user freedom? The answer lies in tools that don’t just manage, they unify.
ManageEngine Endpoint Central is part of that shift. It handles macOS, Windows, iOS, Android, and Linux, and does it from one console. Admins track patch status, app installs, remote activity, and policy compliance without juggling five platforms.
It’s why more CIOs push for platforms that blend IT operations with security oversight. Because in the hybrid era, the endpoint is the front line.
Look, hybrid work is here to stay, and so is device sprawl. But chaos doesn’t have to follow.
Organizations that lean into automation, gain real-time visibility, and enforce unified policies are already winning this war. They are preventing Remote Device Threats at the endpoint level.
Tools like ManageEngine Endpoint Central are rapidly becoming more like a playbook. In this new era, endpoint management is the backbone of hybrid workforce resilience.
Wrapping Up
I hope this blog has offered you a unique perspective on the issue. If you love such informative posts on the latest tools and software, don’t forget to check out our website. I regularly review such tools and software on my website. So feel free to explore.
Till then, be safe, be vigilant, and protect your business from remote device threats.
FAQs
What is ManageEngine Endpoint Central used for?
It helps IT teams monitor, manage, and secure all enterprise devices, including remote endpoints, from a single dashboard.
Why are Remote Device Threats rising in hybrid workplaces?
Remote access, BYOD policies, and unsanctioned apps increase exposure to data leaks, malware, and compliance gaps.
How does Endpoint Central reduce Remote Device Threats?
It automates patching, blocks unauthorized tools, enforces policies, and tracks all device activity in real time.
Can Endpoint Central handle mobile and personal devices, too?
Yes. It supports full mobile device management (MDM) for both personal and corporate-owned devices.
Does Endpoint Central help with data compliance?
Absolutely. It creates audit-ready logs to meet GDPR, HIPAA, PCI DSS, and other security mandates.
Read more from Technology
- Top Ways AI Is Changing Software Development and Product Management
- The Hidden Cost of Network Blind Spots & How ITOM Software Can Fix It?
- Why SIEM tools Lead Compliance in 2025?
- Why Enterprises Want the Best IT Service Desk to Monitor Employee Experience?
- Why Remote Device Threats Are a New IT Headache?
- How to choose the best procure-to-pay software for your business?
- Choosing the Right Enterprise LMS for Your Organization
- The Pros and Cons of Using Generative AI for API Testing
- Top 8 GenAI Trends to Watch in Technology in 2025